.DevOps on AWS like a Rockstar
Aytomic, a software development company, today uses a wide range of AWS services and tools which helps it deliver services and solutions in an efficient way with the minimal operational effort which then again helps it to focus more on the innovation and development.
We at globaldatanet as their AWS DevOps Partner and friends have helped Aytomic to focus on development while taking care of DevOps and Security on AWS. So the solution would definitely go for creating or leverage an existing AWS Transit Gateway, this means that with the TGW you can connect different VPCs in different accounts, manage a single routing table common to all these VPCs or having isolated Routing tables for each VPC (Routing Domains) if you want or need to have fine-grained control of the traffic going in and out of your VPCs. That’s it! Simple as that, let us describe the solution for you and list the resources needed, so we can finally deep dive into the details.
Security Baseline
As a starting point, security, especially at IoT related companies, must be everyone’s primary concern. Having that in mind, we as AWS experts, have helped them to build the secure environment starting with detailed and thorough security assessments and remediation following all the principles and rules from the AWS Well Architected Framework, AWS Trusted Advisor and AWS Security Best Practices.
In addition, we have heavily utilized the AWS Config and CloudWatch alarms to monitor any change in the infrastructure such as changes in IAM policies, root account usages, instance changes, VPC changes, security groups, and NACLs changes and to constantly monitor any suspicious activity or a change that could end with possible security incident or breach.
Logging
Amazon Elasticsearch Service makes it easy to deploy, secure and operate ElasticSearch cluster what gives endless options and possibilities to get the visibility of the data and important metrics in real time. Combining the managed Elasticsearch cluster with CloudWatch subscription filters and Lambda functions, raw platform data can be used as an actionable insight in a quick and secure way.
Data Storage
Data persistence was another requirement and Amazon RDS makes it easy to set up, operate and scale a database in the cloud without heavy lifting, including the provisioning, database setup, patching and backups. It allows a team to focus solely on the actual data and data structuring and modeling, and still having the benefits as fast performance, high availability and security.
To maintain the security, network isolation of resources and integration with IAM provides an additional layer of security together with encryption at rest and in transit.
Golden AMI Pipeline
One of the goals was to build a complete pipeline in order to deliver the Golden AMI as a baseline AMI for all the services. We have successfully built the complete pipeline using only services and tools that are available on the AWS, starting with the existing code repository all the way to the CodePipeline, AWS Systems Manager, Lambda functions, CloudFormation templates, and AWS managed Chef Opsworks server. As part of security guidelines, we have also implemented the AWS Inspector to check the images for known vulnerabilities.
Configuration Management
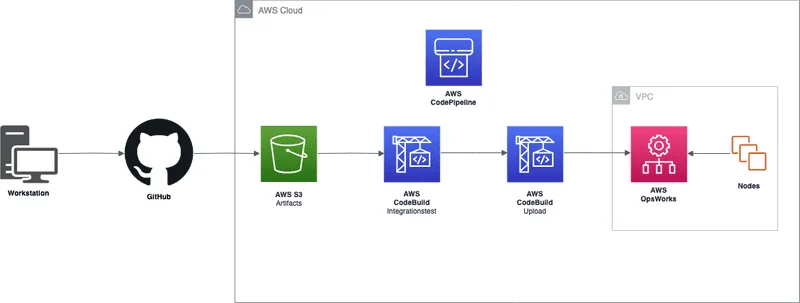
Using the CodePipeline as well as CodeBuild and AWS OpsWorks together with the Chef Automate have helped us to achieve another goal, which is continuous Chef cookbooks integration testing and delivery.
Why this is important for us? Any Chef server should be a hub of tested and trusted cookbooks that could be added to the node run list easily. However, the testing and delivery of the cookbooks to the Chef server can be a tedious task. To simplify this process, we have fully leveraged AWS products and technologies to create a pipeline that executes integration tests and delivers the cookbooks to the Chef server. That allowed automation of a regular and essential part of the cookbook development without any operational overhead.
AWS EC2 SSH keys management with IAM
Using native AWS toolset (IAM) we were able to implement a solution to overcome the burden of AWS EC2 SSH keys management without sharing the keys using the IAM to store and retrieve the public SSH keys together with the sshd’s AuthorizedKeysCommand. Integration with the IAM makes it possible to restrict the SSH access to the specific users and simplifies EC2 SSH keys management at a single point.
Background information
At Aytomic we provide custom software solutions. We have a team of highly experienced developers and we have experience in IoT engineering (hardware design and firmware development), mobile development and software architecture.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
