.Encryption of SSM session data using KMS
Connecting to your EC2 Instances using Session Manager is for years already a default. However most of the users are just using the defaultTLS 1.2 encryption that AWS already provides by default. For most of the usecases this is ok, but sometimes it is required to encrypt your sessions with your own KMS Keys. Encrypting session data with your key also enables sessions to handle confidential data interactions, such as password resets, and further improves your security posture when using Systems Manager Session Manager. To use the option to encrypt session data using a key created in AWS KMS, version 2.3.539.0 or later AWS Systems Manager SSM Agent must be installed on the managed instance.
In addition i would also recommend to log the session data either to S3 or to CloudWatch and to encrypt the session data which is logged to the destination using your own KMS Key. In the following post I will explain how to automatically configure the SSM default settings to secure your session data using your own KMS key.
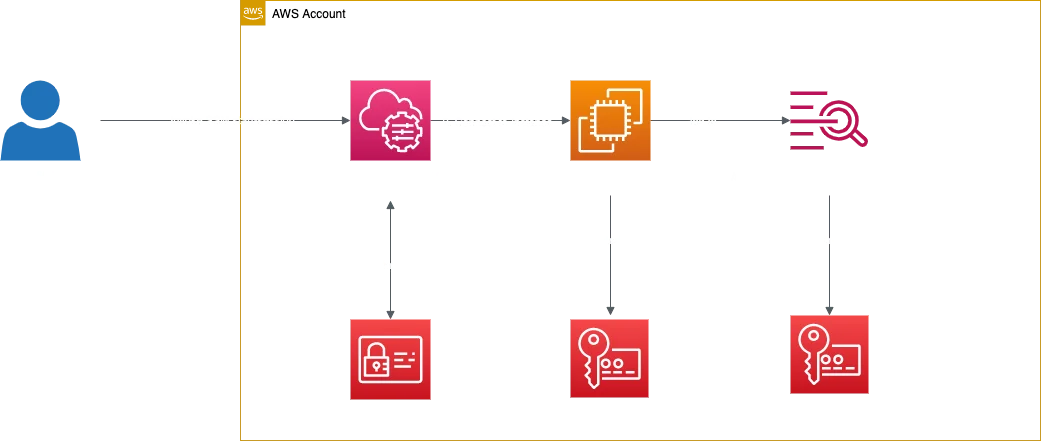
Setup
- Set up the required KMS Keys using this template using StackSet or Stack - this template will create the needed KMS Keys for SSM and CloudWatch with permissions.
- Create a LambdaLayer with
boto3or use a prebuild layer. - Deploy the following template using StackSet or Stack - the template which I provided will configure your Session Manager.
After successful deployment:
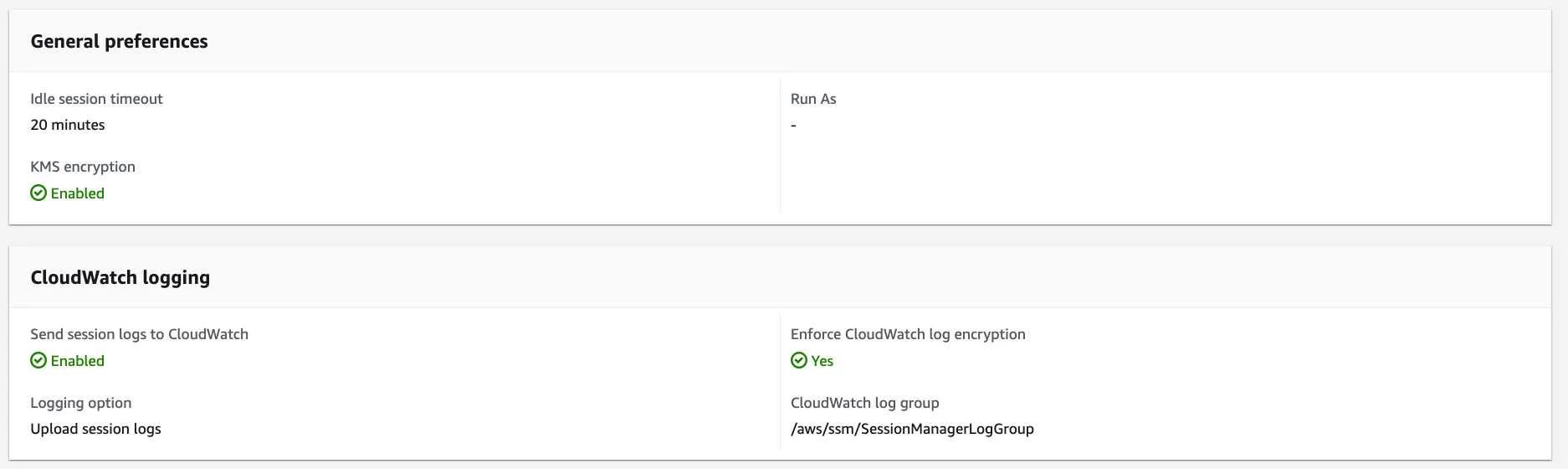
4. Optionally secure CloudWatch LogGroup using SCPs. Since the CloudWatch LogGroup from Session Manager will contain sensitive data, I would recommend to secure the LogGroup using SCPs so that only a few people from your audit team can read them.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "CloudWatchLogsDeny",
"Effect": "Deny",
"Action": [
"logs:DescribeLogStreams"
],
"Resource": [
"arn:aws:logs:*:*:log-group:/aws/ssm/SessionManagerLogGroup:*"
],
"Condition": {
"ArnNotLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:role/AuditRole"
]
}
}
}
]
}Usage
Now you can either use your browser or CLI to connect to your instance using the Session Manager and during the session all data will be encrypted using your own KMS Key.
ℹ️ You can not use aws ssm start-session with the --profile flag that needs a MFA because there is an 🚨 issue right now that the command doens't ask for MFA.
Workaround: Using awsume solves this problem.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
