.Security as the foundation of digital sovereignty
Any organization processing and storing data of any form is potentially a target of cyber-attacks. Therefore you need to protect your data against such attacks. Especially when you are handling sensitive data. That is why security is an important main pillar of digital sovereignty.
Security is not just about protecting against unauthorised access and cyberattacks. It is also about ensuring the resilience, compliance and reliability of your digital assets. This is achieved through strict access controls and robust authentication mechanisms that protect your data from breaches. By implementing robust security measures, you can protect your customers' data and ensure compliance with relevant regulations, such as General Data Protection Regulation (GDPR) or DORA (Digital Operational Resilience Act).
Beyond technical measures, security fosters trust, as customers and partners are more likely to engage with organisations that prioritise data protection, making it a fundamental aspect of credibility and digital sovereignty. On the other hand companies which have security incidents additionally suffer from big losses in their reputation.
In summary, with security you want to:
- Protect Data - Implementing least privilege and encryption protect data and counter the rise of threats.
- Comply with regulations - Ensure compliance and meet legal requirements for your data, such as GDPR.
- Maintain customer confidence and trust - Build trust by protecting privacy and demonstrating a commitment to digital sovereignty.
Security in the Cloud
Securing the cloud is a dynamic and critical process that requires a blend of robust technical controls, well-defined organizational policies, and proactive continuous monitoring. By addressing the unique challenges of cloud environments with a structured approach, you can safeguard data, applications, and infrastructure against evolving threats.
Here's a comprehensive guide to achieving and maintaining cloud security:
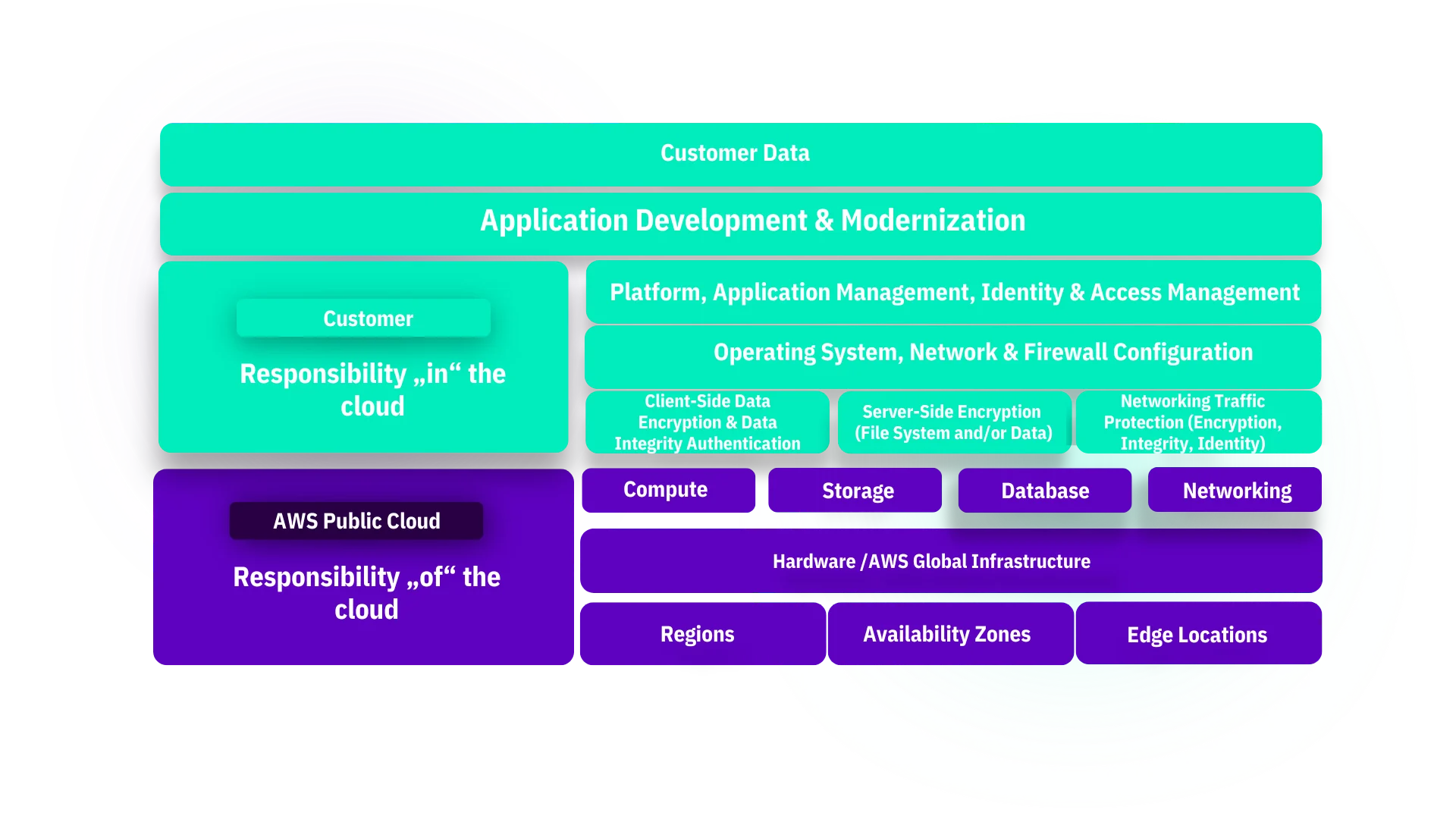
Shared Responsibility
AWS shares the responsibility for security and compliance with you. AWS manages and controls infrastructure components such as physical security, the virtualisation layer, and the host operating system.
You as a Customer are responsible for managing the security in the cloud like guest operating system, application software, updates, patches, and security configurations, such as firewalls and access permissions.
Identity and Access Management (IAM)
Identity and access management helps you to securely manage and scale access to your resources, between your resources and for your employees.
- Using temporary security credentials and permission sets enhances security by minimizing the risk of long-term credential exposure, enabling controlled, time-bound access to AWS resources.
- AWS Identity Center, you can efficiently manage workload and workforce identities by managing user access within a single AWS account or centralising identity management across multiple accounts for seamless and secure authentication and authorisation.
- Access Analyzer helps you identify and remove unused or external access to resources, and create least privilege policies to limit access to only what's needed
For a deep dive into centralised permission management at scale with AWS IAM Identity Center, check out this post.
Detection and Response
AWS provides comprehensive detection and response capabilities through services such as Amazon GuardDuty as an intrusion detection system (IDS) for threat detection and AWS Security Hub for a single view of all security alerts. Amazon GuardDuty continuously analyses network traffic and uses multiple workload and account logs to detect threats using anomaly detection, AI, ML, and threat intelligence. The service integrates directly into the AWS landscape and automated response mechanisms can be used to automatically remediate the threat.
Data Protection
To achieve data protection, you need to focus on three important pillars: Data classification, protection of data at rest and protection of data in transit.
- Data Classification helps you categorize your data based on its importance and sensitivity, providing a foundation for determining the appropriate protection and retention controls. AWS services like Amazon Macie can help automate this process.
- Protecting Data at Rest is a must. In AWS, you can use AWS Key Management Service (KMS) to encrypt data for your workloads and apply least privileges access policies to your encryption Keys. Additionally, you can bring your own key material using a Hardware Security Module (HSM) and integrate it with KMS through the External Key Store (XKS) feature, enabling seamless encryption across AWS services.
- Protecting Data in Transit is crucial to ensure secure communication between systems. AWS provides a Service called AWS Certificate Manager (ACM) to manage SSL/TLS certificates, making it easier to enforce secure connections across your workloads.
For handling confidential data, AWS provides the Nitro system – a specialized hardware security solution that ensures complete isolation of virtual machines.
Compliance
AWS helps you to comply with the legal requirements and compliance for your data by providing you tools and services that help you to comply with various laws and regulations. AWS itself is already certified and fulfils numerous standards such as ISO 27001 or C5 (BSI requirements for cloud providers). So that you can monitor the compliance status of your resources, there are services such as AWS Config that monitor resource changes and check them according to applicable regulations. You can also use automated audit processes with the AWS Audit Manager to check how well your regulations are being met.
Network and Application Protection
Network and application protection in AWS is essential for securing your infrastructure and services against unauthorized access and attacks.
AWS offers services to protect applications from common internet attacks. These include DDoS attacks, which can compromise security and availability. If you want to learn more about web application firewalls, check out our Web application Firewalls at Scale Service.
Amazon VPC lets you create isolated network environments to manage traffic with security groups and NACLs. AWS Security Groups function as virtual firewalls for virtual instances like EC2, controlling inbound and outbound traffic.
Conclusion
Robust security is essential for every organization handling data, especially sensitive information, to protect against cyberattacks and ensure compliance. AWS offers various services to safeguard data and manage access effectively. Security helps you build trust, stay compliant and keep your digital assets safe.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
