.AWS IAM Identity Center Permission Management at Scale Part 2
If you start working with AWS IAM Identity Center (successor to AWS SSO) you will learn, that on the one hand, the console is not as intuitive as other AWS consoles. On the other hand, you will notice, that takes a lot of work to manage permission sets and their assignments if you work with lots of accounts and users/groups of your AD.
Before we have a deeper look at our solution, let's start with some basic background information of the AWS IAM Identity Center itself.
Permission Set
A permission set is basically a set of managed and custom IAM policies, which you can assign to a user/group in an account.
Account Assignment
An account assignment is the core of provisioning roles in an account and assigning them to a user/group:
As you already know from AWS Best Practices guides for IAM you should only assign permissions to IAM groups. With AWS IAM Identity center we follow the same path. With the provided solution we only assign groups in our Account Assignments.
Identity Store
When you enter Identity Store in the search bar of the AWS Console, you will get AWS IAM Identity Center (AWS IAM IC) as a result. Under the hood (SDK/API/CLI), it is a dedicated service, which will manage the users and groups synchronized from the configured identity source in AWS IAM Identity Center.
What is the challenge to manage the Account Assignments?
If you want to use AWS IAM Identity center at scale, you will ask yourself, how to provision a set of IAM roles for all accounts? Or if you have a structured AWS Organization (landing zone) with lots of Organizational Units (OUs) you also might want to provision IAM roles only in accounts of a dedicated OU. As a surprise you will find out, that there is no managed way in AWS IAM Identity Center, which will help you, to achieve this goal. You have to create all Account Assignments explicitly (via Console/CLI/SDK/API).
But what happens, if you e.g. created Account Assignments for a permission set, which has to be provisioned in all accounts and you created a new account? Correctly. You have to create it afterward. So there is no automated mechanism for managing Account Assignments. This will massively increase the work of the people, which are responsible for your permission management.
And this is where our solution of automated management for Account Assignments comes in.
Provisioning of Permission Sets and Automated Management for Account Assignments
🔗 Here you can find the Solution on Github
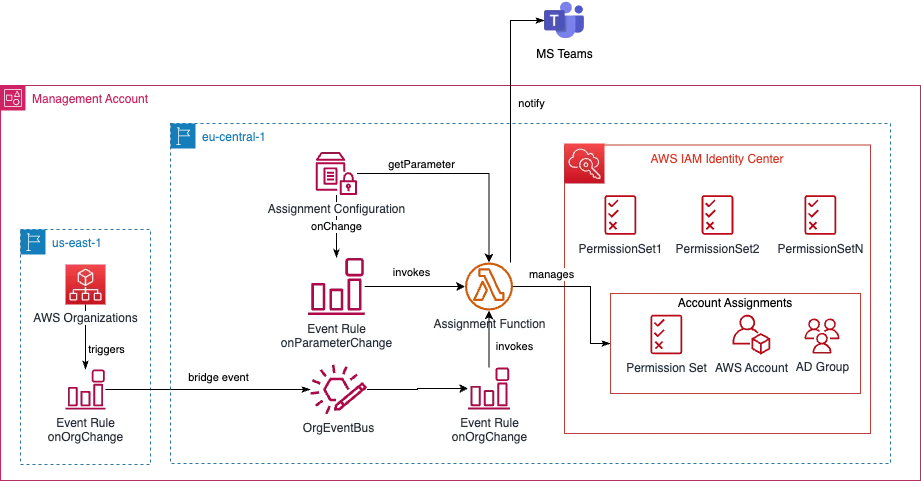
In our CDK based project several resources will be provisioned due deployment. It contains of two stacks.
The first stack contains:
- permission sets with IAM policies (provided by you)
- a lambda function that will do the math (managing account assignments)
- an SSM parameter to store the provided configuration for assignments
- an event rule for changes on the above parameter which will trigger the lambda function
- a custom event bus for bridging AWS Organizations CloutTrail events (see second stack) and an event rule which listens on it and will trigger the lambda function
- all necessary IAM roles and permissions for the lambda function
The second stack will provision:
- an event rule in
us-east-1region to bridge CloudTrail events from AWS Organizations (which are only available inus-east-1)
The lambda function can also be configured to notify via MS Teams, when the Assignment Function creates or deletes assignments in your management account.
The configuration of the stack is done in a dedicated configuration file:
export const SampleConfig : Config = {
General: {
IdentityStoreId: "<Your identity store id>",
SsmParameterName: "/YOURORG/ASSIGNMENTCONFIG",
SsoInstanceArn: "arn:aws:sso:::instance/ssoins-<IdOfYourSsoInstance>",
TeamsWebhookUrl: "https://yourorg.webhook.office.com/webhookb2/webhookid"
},
AssignmentConfiguration: {
// place your assignment configuration
},
AssignmentFunction: {
MemorySizeMb: 1024,
TimeOutSeconds: 300
}
}What you have to configure:
How to configure the automation for Account Assignments
In the section AssignmentConfiguration section, you can place the desired configuration for account assignments. You can place:
- Global Assignments: Permission Sets and AD Groups have to be assigned to all accounts
- OU Assignments: Permission Sets and AD Groups have to be assigned to all accounts of an organizational unit in AWS Organizations (you have to specify the OU name)
- Account Assignments: Permission Sets and AD Groups have to be assigned to dedicated accounts (you have to specify the account name)
Sample Configuration:
The Assignment Configuration will be stored in the SSM Parameter via CDK deployment. Every change will be updated in the Parameter and will trigger the lambda function.
AssignmentConfiguration: {
AdDomain: "yourorg.com",
GlobalAssignments: [
{
AdGroupName: "AD-GROUP-CLOUD-ADMINS",
PermissionSet: "MyRole1PermissionSet"
}
],
OuAssignments: [
{
OuName: "FinanceUnit",
Assignments: [
{
AdGroupName: "AD-GROUP-FINANCE-OPS",
PermissionSet: ""
}
]
}
],
AccountAssignments: [
{
AccountName: "MyOrgSecurityAccount",
Assignments: [
{
AdGroupName: "AD-GROUP-SEC_AUDIT",
PermissionSet: ""
}
]
}
]
}How the automation with the lambda function works
The Assignment Function is triggered by Event Rules of AWS EventBridge. As already described in the solution overview, there are two different event rules in place:
- AWS Organizations Events: CreateAccount, CloseAccount, MoveAccount, CreateOrganizationalUnit, DeleteOrganizationalUnit, UpdateOrganizationalUnit, RemoveAccountFromOrganization
- AWS SSM Parameter Events: Create, Update, LabelParameterVersion
Here is how the function works:
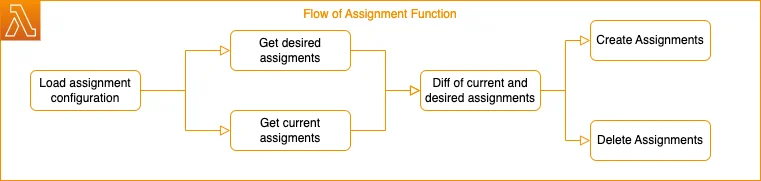
- Loads the assignment configuration from the SSM Parameter
- Get a list of all desired and current deployed account assignments
- Make a diff of the list to get the assignments, which have to be created/deleted
- Create/Delete assignments
- Notify MS Teams on successful/failed assignment creations/deletions
Conclusion
With our provided solution you can provide assignments for permission sets, which will be automatically managed by the Assignment Function for
- all active accounts in your AWS Organization
- all active accounts in an OU of your AWS Organization
- a dedicated account in your AWS Organization
The Assignment Function listens to major events of your AWS Organization to automatically create/delete assignments based on your Assignment Configuration.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy

