.Improved Networking For AWS Lambda
AWS announced a major improvement to how AWS Lambda functions work with your Amazon VPC networks. You will see dramatic improvements to function startup performance and more efficient usage of elastic network interfaces.
In case a Lambda function is not configured to connect to your VPCs then the function can access anything available on the public internet including other AWS services, HTTPS endpoints for APIs, or endpoints and services outside AWS. So, the function has no way to connect to your private resources that are inside your VPC.
When the Lambda function is configured to connect to your own VPC, it creates an elastic network interface within the VPC and does a cross-account attachment.
With this model, there are a number of challenges that you might face. The time taken to create and attach new network interfaces can cause longer cold-starts, increasing the time it takes to spin up a new execution environment before your code can be invoked.
As your function’s execution environment scales to handle an increase in requests, more network interfaces are created and attached to the Lambda infrastructure. The exact number of network interfaces created and attached is a factor of your function configuration and concurrency.
What has changed?
AWS Hyperplane for providing NAT
The team is using AWS Hyperplane, the Network Function Virtualization platform that is used for Network Load Balancer and NAT Gateway. It also has supported inter-VPC connectivity for AWS PrivateLink. With the help of Hyperplane the team will provide NAT (Network Address Translation) capabilities from the Lambda VPC to customer VPCs.
### Network interfaces within VPC are mapped to the Hyperplane ENIThe Hyperplane ENI (Elastic Network Interfaces), a network resource controlled by the Lambda service, allows multiple execution environments to securely access resources within the VPCs in your account. So, in the previous model, the network interfaces in your VPC were directly mapped to Lambda execution environments. But in this case, the network interfaces within your VPC are mapped to the Hyperplane ENI.
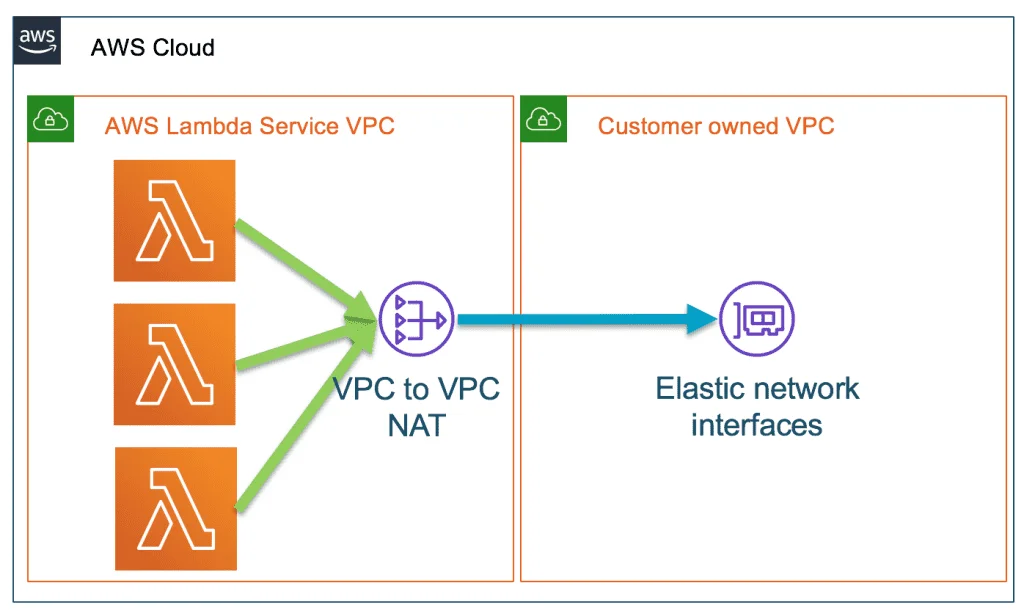
While Hyperplane still uses a cross account network interface, it provides the following benefits for Lambda within a VPC:- Reduced latency when a function is invoked by using pre-created network interfaces. The network interface is created when the Lambda function is initially created.- Network interfaces are shared across functions with the same security group:subnet combination- Function scaling is no longer bound to the number of network interfaces
Developers don’t need to enable this new capability and AWS is gradually rolling this out across all AWS regions over the next couple of months.
While the new changes make it more conducive for developers to connect Lambda functions to VPCs, the basic architecture doesn’t change in terms of your VPC.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
