.Introducing the AWS Firewall Factory
A few days ago we introduced our AWS Firewall Factory. A simple solution that helps you deploy, update, and stage your Web Application Firewalls while managing them centrally via AWS Firewall Manager.
What are Web Application Firewalls?
AWS Web Application Firewalls (WAFs) protect web applications and APIs from typical attacks from the Internet that can compromise security and availability, and put undue strain on servers and resources. The AWS WAF provides prebuilt security rules that help to control bot traffic and block attack patterns. However, with its help, you can also create your own rules based on your specific requirements. In simple scenarios and for smaller applications, this is very easy to implement on an individual basis. However, in larger environments with tens or even hundreds of applications, it is advisable to aim for central governance and automation. If you want to learn more about this solution or Web application firewalls in general feel free to register to this event.
Architecture
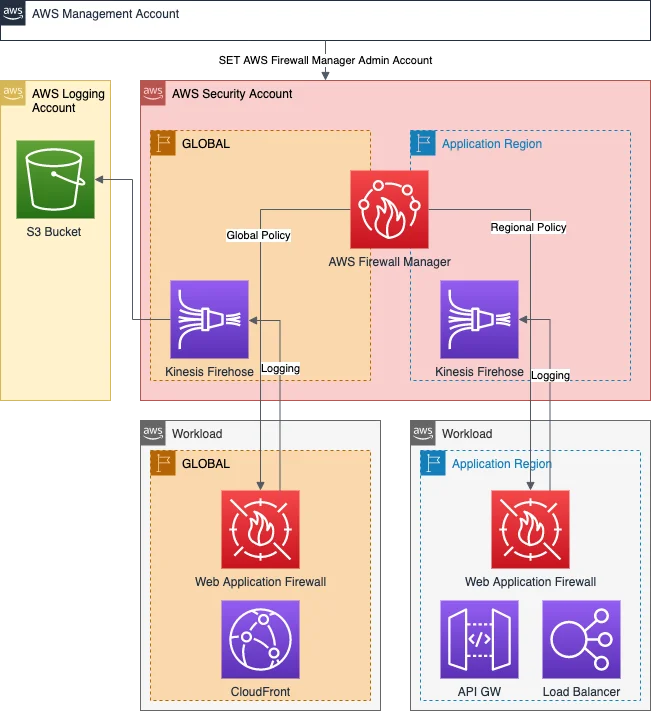
Let's take a quick look at the solution architecture. In order to be able to provision WAFs using AWS Firewall Manager to other accounts we first need to set the Firewall Manager administrator account in our AWS Organization. Additionally we need to have a central S3 Bucket which we will use for our WAF logs. The logs we could use to see potential false positives to develop custom WAF rules. The easiest way to do this is to query the S3 bucket via Athena.
But first you should just start with ManagedRuleGroups to have a base set to secure your applications. AWS Managed Rules for AWS WAF is a managed service that provides protection against common application vulnerabilities or other unwanted traffic, without having to write your own rules.
After deploying your first firewall and using ManagedRuleGroups to detect errors in your application, you can use aforementioned s3 log bucket to create queries and define your own custom rules using the false positives. You do this simply by defining the RuleStatements around your statements in your value file. During the deployment process, the solution calculates the required capacity using the CheckCapacity API from AWS and creates RuleGroups that are attached to the WAF. We have also developed an algorithm that pads the RuleGroups to the maximum RuleGroup size and only then creates a new RuleGroup.
All settings where the WAF should be deployed and with which settings (should be made) are controlled via the dedicated value file. Currently we only support a deployment via Taskfile. Later we will also support deployments via Teamcity.
Currently implemented Features
- Automated Capacity Calculation via API - CheckCapacity
- Algorithm to split Rules into RuleGroups
- Automated Update of RuleGroup if Capacity Changed
- Add ManagedRuleGroups via configuration file
- Automated Generation of draw.io diagram for each WAF
- Checking of the softlimit quota for WCU set in the AWS Account (Stop deployment if Caluclated WCU is above the quota)
- Easy configuration of WAF Rules through json file
- Deployment Hash to deploy same WAF more than one time for testing and/or blue/green deployments.
- Stopping deployment if soft limit will be exceeded: Firewall Manager policies per organization per Region (L-0B28E140) - Maximum number of web ACL capacity units in a web ACL in WAF for regional (L-D9F31E8A)
- NEW RegexMatchStatement and IPSetReferenceStatement is working now 🚀
We hope you'll find this solution helpful to secure your environment! If you have any feedback about the solution, please feel free to reach out to us or open a github issue.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
