.Secure handling of AWS api keys
At globaldatanet we always advocate a strong authentication when interacting with the AWS APIi. We happily recognize that SSO is now a part of the AWS CLI Version 2, but in our projects we still have to handle local IAM API access keys for our development and our customers. To mitigate the drawback of storing sensitive date as cleartext in your credentials file, we use AWS-Vault to store and access the API keys in a secure way.
How it works
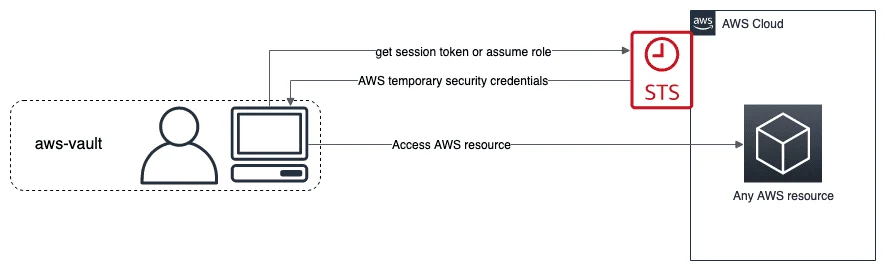
AWS Vault is an opensource tool published under the MIT license. It stores IAM credentials in your local securtiy store. AWS Vault supports security backends for Mac OS, Linux and Windows. It is using the stored credentials to request temporary credentials from Amazons's STS service. Temporary credentials have a limited lifetime which reduces the risk of leaking. The temporary credentials are then exposed as environment variables to the executed process.
Installing
$ brew cask install aws-vault Warning: Cask 'aws-vault' is already installed.
Configuration
First you need to store new credentials in your vault.
aws-vault add test Enter Access Key ID: ABDCDEFDASDASF Enter Secret Access Key: 8TdTeIxTNunauw3ZlPhG72i9XU7j10HAFHJhzKY9 Added credentials to profile "test" in vault
Execute any command.
$ aws-vault exec test -- env | grep AWS AWS_VAULT=test AWS_DEFAULT_REGION=eu-central-1 AWS_REGION=eu-central-1 AWS_ACCESS_KEY_ID=%%% AWS_SECRET_ACCESS_KEY=%%% AWS_SESSION_TOKEN=%%% AWS_SECURITY_TOKEN=%%% AWS_SESSION_EXPIRATION=2020-03-24T15:15:40Z
For the full documentation check out the Github repository.
Tip
If you execute aws-vault without additional commands, it will start a new shell and expose the environment variables in this sub shell.
$ aws-vault exec test $ grep env AWS AWS_VAULT=test AWS_DEFAULT_REGION=eu-central-1 AWS_REGION=eu-central-1 AWS_ACCESS_KEY_ID=%%% AWS_SECRET_ACCESS_KEY=%%% AWS_SESSION_TOKEN=%%% AWS_SECURITY_TOKEN=%%% AWS_SESSION_EXPIRATION=2020-03-24T15:15:40Z
Github
Further information and the source code can be found here:
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
