.The basics of isolating tenants in your SaaS application on AWS
For companies without existing experience, multi-tenant isolation can be overwhelming. Every business needs to evaluate business challenges and align solutions accordingly to their needs. This blog is intended to introduce you to the basics of implementing tenant isolation on AWS and why it does matter.
B2B SaaS
SaaS integration can be a major step-up for companies of every size. Start-ups, small-to medium sized organizations and enterprises can profit from it. As a company grows, adaptation of software and perfectly fitted solutions can play a crucial role in achieving company growth while simultaneously focusing on a company's unique selling proposition.
Providing companies with expertise on AWS Cloud, Serverless and B2B SaaS can lay the foundation for reliable, secure and professional ways to ensure growth, reach, and innovation.
Serverless Adaptation Of SaaS
More and more AWS partners that leverage programs, expertise and resources, building innovative solutions, shift towards SaaS to adopt shared infrastructure models to achieve cost and operational efficiency. With Serverless you only pay for what you use. Systems predict usage and therefore offer not more than you actually need.
Effort management in SaaS often tries to anticipate and map tenant’s consumption of infrastructure resources. Loads can vary depending on tenant's activity. Infrastructure needs to respond correspondingly. Here Serverless comes in handy as it is functioning on similar principles.
As the demand for cloud-native architecture increases, security demand also does. It is crucial for companies to sync their knowledge and cooperate with teams that have expertise in securing multi-tenant environments.
Determining how these environments will ensure that tenants are prevented from accessing another tenant's resources is one challenge every SaaS provider has to take on, as an essential part of SaaS. Without the safety of multi-tenant isolation, there is no successful SaaS. Therefore every SaaS provider needs to concept their design and development around fundamentals like actively supporting customers according to their business needs, to understand the level of isolation required.
What is Isolation?
Companies often think about isolation through a security and compliance lens. It creates boundaries to limited resources of multi-tenant platforms and deals with concerns about performance and so-called noisy neighbors. These are two different viewpoints of isolation, but both need to be addressed.
Noisy Neighbors
You can buy a house or rent an apartment.
Costs and administrative work are drastically higher if you buy a house while living in an apartment means you might have to give up some of your privacy to save the extra money.
Applying this on a business IT infrastructure is similar but there are more solutions for that. In shared infrastructures, applications might use a majority of available resources and therefore cause network problems for other existing applications, just like a noisy neighbor. This issue is as old as the start of the world wide web and web applications.
What is enough isolation?
Even though challenges are common, there is no one-fits-all solution, therefore strategies are various. Domain, compliance, deployment model and selection of AWS services bring unique considerations to tenant isolation and every SaaS provider has their definition of isolation.
Things every SaaS provider agrees on:
Isolation is not an option.
There is no universal solution.
For example, having controlled access through authentication and authorization of your Saas environment is not enough as this is a basic level expectation.
Isolation is not a customer specific topic as it is not unrealistic for developers to cross a line of tenant isolation in the development process. This risk is solved through a controlled shared mechanism like applying isolation rules.
There are a lot of scenarios where existing tools can not address an isolation model directly so let us look into the specific isolation concepts to gain a better understanding. We will compare the Silo Isolation Model with the Pool Isolation Model and the Bridge Isolation Model. Let's start with Silo Isolation:
Silo Isolation
This model runs a fully or partly separated siloed stack of resources. Each customer stack construct is built end-to-end but with implemented basics of SaaS like shared identity, onboarding, metering, metrics, deployment, analytics and operations. Siloed deployment models use technologies to surround the tenants stack within an encapsulated environment.
Key-Take-Aways:
- For preferably stricter compliance isolation environments
- No noisy neighbors
- Easy Tenant cost & error tracking
- Limited scaling & agility
- Higher Costs
- No decentral management
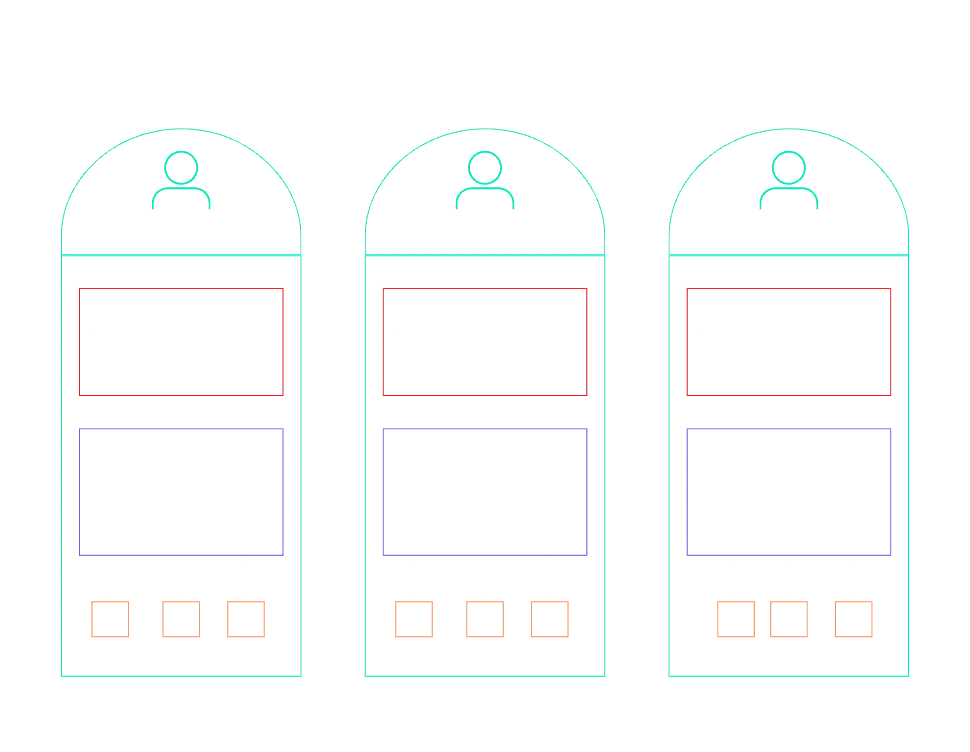
Pool Isolation
When a model is based on a shared infrastructure with cross-tenant access, we call it a pool. This is the result of companies, aiming at optimizing efficiency, agility and cost through sharing underlying infrastructure. As you already might have noticed, it is more complex to ensure reliable cross-tenant access.
Key-Take-Aways:
- Efficiency through agility and cost benefits
- Resources scale proportionally according to loads imposed by tenants
- Simplified management and operations with one view into the whole system
- Potential of existing Noisy neighbors
- More complex tenant cost & error tracking
- Portions of system still may need to be siloed
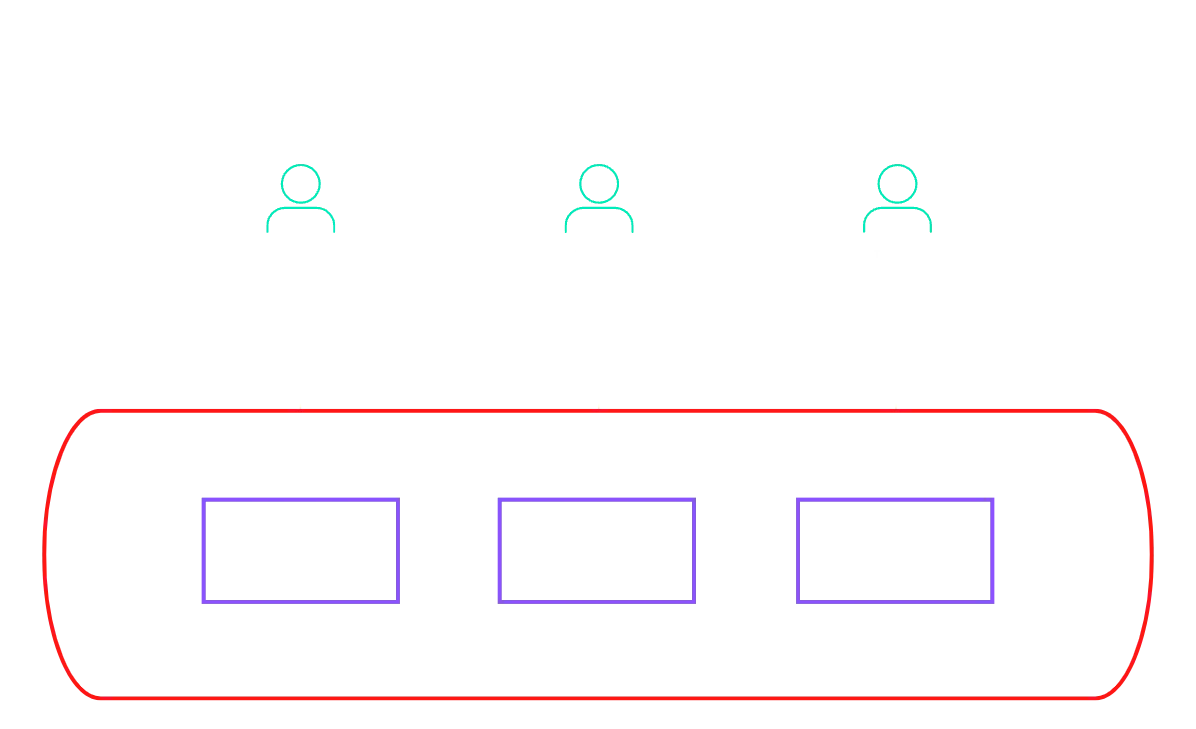
Bridge Model
Now we get into even more specific environments as the bridge model is a mix of silo and pool models depending on the specification of integrated services. For example based on a tier system where web tiers are shared in a pool model while business logic and storage are siloed in specific app tiers.
Key-Take-Aways:
- Using Silo and Pool to specify infrastructure for more complex needs
- Models for each layer of architecture
What are Tiers?
Like mentioned above, a tier offering is a form of multiple isolation packages with different profiles to combine and address customer needs more precisely. Tenants run in a shared infrastructure model but expect fully secured ressources. With a tier based solution, customers with higher compliance requirements can pay a premium to be deployed in a more siloed model.
But more often SaaS providers try to limit these as they might fall back into the cons of siloed models mentioned above.
Identity and Isolation
Identity is not just another concept model of isolation. It is more like a different aspect of isolation that needs to be addressed in every multi-tenant environment. Key factors are the representation and identification of tenants currently accessing resources. To master this challenge SaaS providers need to consider combinations of shown isolation strategies and identity policies and scoping rules.
Let's keep in mind:
The primary focus should be on the customer needs and integrating models they are benefiting from. Infrastructure can be as individual as a company itself, therefore it is important for companies of every size to adjust operations to scale according to their business. With SaaS on AWS you can profit from already built solutions and with the right AWS partner to your side you will master this challenge. By reducing the time spent on operational tasks and focussing more on what makes your business unique, we all profit from faster innovation.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
