.Automating AWS IAM Identity Center Setup Part 1
If you start working with AWS IAM Identity Center (successor to AWS SSO) you will learn after a short time that there is no official AWS SDK available to do the initial setup of an AWS IAM Identity Center instance and also to add a configuration that users or groups will be synced from your identity source to the AWS IAM Identity Center instance. Therefore we decided to use the Coto - the undocumented AWS Management Console APIs SDK for Python as a source and reverse-engineered the AWS calls for setting up an AWS IAM Identity Center instance and syncing ad users/groups to write our own client for Coto to automate the whole setup.
First, we would like to give you some basic background information on the AWS IAM Identity Center itself.
Identity source
The identity source in IAM Identity Center determines where your users and groups will be maintained.
⚠️ Limitation: Only one identity Source per AWS Organization can be selected.
The following identity source is available:
- Identity Center directory (Default)– Users and Groups will be managed in AWS IAM Identity Center
- Active Directory – Manage User in your own self Hosted or AWS Managed Active Directory
- External identity provider – Manage your user in an external identity provider (IdP) such as Okta or Auth0.
Sync Filters
Sync Filters define the identities to sync from your Active Directory or External identity provider. You can define User or Group Sync Filters.
Identity Store
When you enter Identity Store in the search bar of the AWS Console, you will get AWS IAM Identity Center (AWS IAM IC) as a result. Under the hood (SDK/API/CLI), it is a dedicated service, which will manage the users and groups synchronised from the configured identity source in AWS IAM Identity Center.
Init Setup of AWS SSO
🔗 Here you can find the Solution on Github
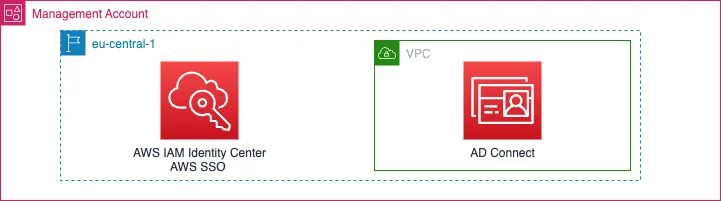
Prerequisite:
- Identity Center must be enabled in your Organization
- Existing AD Connect (for this example - Script can be adjusted to use different Identity Sources) -> Here you can find a repository with automation to create an AD-Connect via CDK
How to configure the initial setup of the AWS IAM Identity Center
Setting up AWS IAM Identity Center from scratch includes a few steps:
- Removing old configuration settings including:
- Directory Associations
- Sync Profiles
- Associating your selected Directory to SSO Instance in your AWS region.
- Creating Sync Profile -> holds the information of the connected Directory
- Creating Test Sync Filter -> creating a first synchronisation target could be a Group or User
- Creating Sync Target -> Connects Sync Profile with SSO Instance Identity Store
- Start Synchronisation -> Starts User / Group synchronisation to your AWS SSO Instance Identity Store
We have created a small script for you which will take care of this steps, you just need to adjust few variables. To invoke the script you just need to follow the instructions in the Readme.
Sync AD Groups to AWS IAM Identity Center (successor to AWS SSO)
🔗 Here you can find the Solution on Github
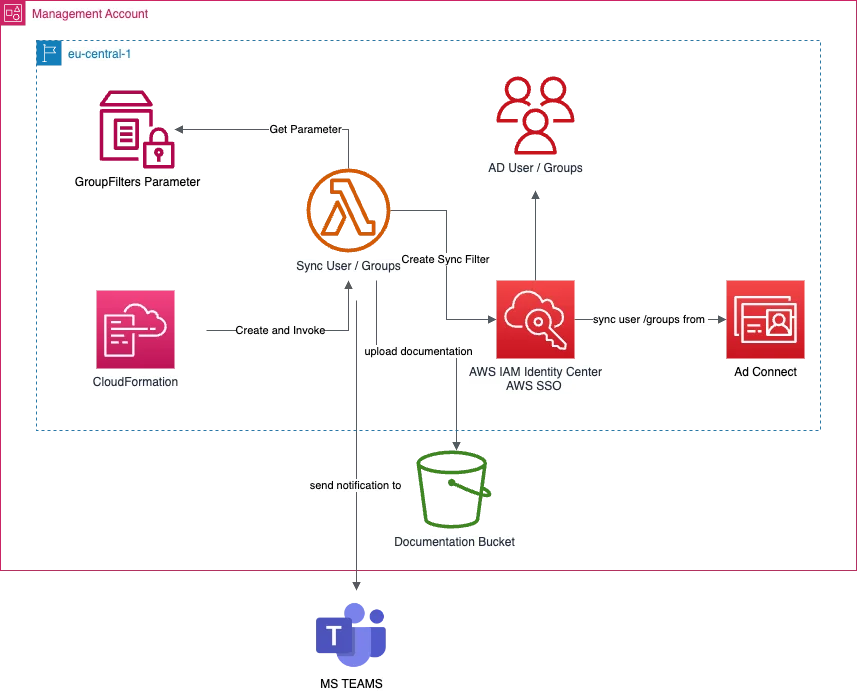
In our CDK based project several resources will be provisioned due deployment.
The Stack contains:
- Parameter Store Parameter which is holding the information which Groups will be Synchronised to our AWS IAM Identity Center
- Lambda Function to create the Synchronisation Filter in AWS IAM Identity Center
- all necessary IAM Roles and Permissions for the Lambda Function
How to deploy the automation for Syncing AD User / Groups
The deployment of the solution is done via a TaskFile which is part of the solution's repository. All the required Parameters will be configured in a json file - an example.json file is also included in the repository.
The configuration of the stack is done a dedicated configuration file:
{
"general": {
"produkt": "SSO-AD-GroupSync",
"stage": "TEST",
"prefix": "COMPANY",
"s3_DOKUBUCKET": "S3_DOKUBUCKET",
"WebhookUrlTeams": "TEAM_WEBOOK",
"DocuWebsite": "Link_to_the_Website_where_the_generated_HTML_snippet_has_been_published"
},
"SSO": {
"ad_DomainName": "DOMAINNAME_of_Managed_Directory_Service",
"GroupFilterConfig":
{
"GroupFilters":
[
{
"Name": "AD_GROUP_NAME",
"Description": "AD_GROUP_DESCRIPTION"
}
]}
}
}
What you have to configure:
The Group Filters will be stored in the SSM Parameter via CDK deployment. To add more Groups or remove Groups from Synchronisation into AWS IAM Identity Center you just need to update your configuration json file and update the Stacks - you will get more information about the lambda functionality in the next section.
How the automation with the lambda function works
The Sync User/group Function is triggered by AWS CloudFormation after Create / Update or Deleting the Stacks after the GroupFilters Parameter was successfully to ensure that the latest changes of the configuration will be deployed.
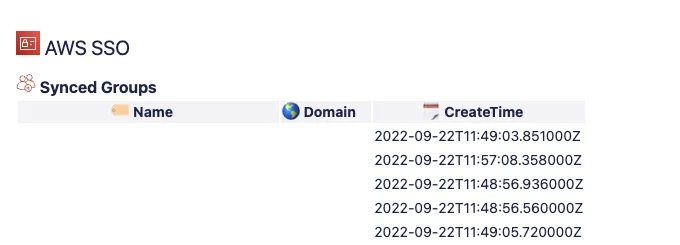
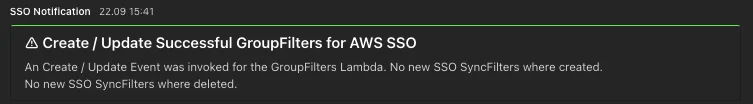
After successful run of the Sync User / Group Lambda function you will find a documentation of the current synced Users / Groups as html in your documentation Bucket + if you added an MS Teams Web-hook also a notification of the implemented Sync Filters during the last run.
Example Documentation:
Example Message:
Open Source
Since we want to give something back to the community, we have published the complete code of the solution freely on Github. We hope you'll find this solution helpful to setup your AWS IAM Identity Center! If you have any feedback about the solution, please feel free to reach out to us or open a github issue.
Conclusion
With this Solution you will be able to configure the AWS IAM Identity Center / AWS SSO from scratch using AWS AD Connect. Moreover you will be able to Sync your Identities automatically with a an ongoing documentation to help you to archive compliance.
If you want to learn how to managed AWS IAM Identity Center Permissions at Scale take a look at the second post of our AWS IAM Identity Center Series.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy

