.Your first line of defense in 2023 to prevent security breaches
2023 does not seem to be a good year for many companies that underinvest in their security. With over 600 known cases of breaches from small, mid to large enterprises and an average cost of $4.45 million (IBM Report), security still doesn't seem to be a top priority topic of conversation for many companies. With the alarming fact that 82% of all breaches in 2023 involved some kind of cloud environment, where access was gained to data stored in the cloud - public, private, or multiple environments, companies must prioritize implementing strong security measures.
A recap of most painful breaches so far in 2023
Rising stars are the prime target for hackers.
For example, one of the most popular online payment service provider got hit by a Credential Stuffing attack in January where cyber attackers successfully accessed about 35,000 accounts. This attack method involves using stolen or illegally obtained login details on multiple services, exploiting users who reuse the same usernames and passwords.
Germany’s health sector is under attack.
Another significant breach leaked in early 2023. A cyberattack led to data leakage of insured patients' information from a health IT service provider. The breach affected millions of individuals in Germany and raised concerns about the security of connected health systems across Europe.
If hackers succeed once, they will come back.
In late April 2023, the same service provider experienced another cyberattack, leading to ongoing disruptions in over 80 health insurance companies that experienced outages and disruptions.
Money can be earned back, but trust is difficult to regain.
Recently, a globally known file transfer tool experienced a breach on the 1st of June, 2023, affecting over 200 organizations and up to 17.5 million individuals. Among those affected are world-wide known companies but also several local health insurance organisations in Germany. Furthermore, a global telecommunications provider was also hit. It not only cost them hundreds of millions of dollars but also the trust of many customers worldwide.
2023 in terms of breaches (so far)

How do you prevent these breaches now?
You can start by implementing a Web Application Firewall (WAF). Here are 8 key takeaways about ways of protecting your application with a WAF:
1. Protection against known vulnerabilities: Just like how you shield yourself from known risks, a WAF defends your web applications from potential breaches like SQL injection and cross-site scripting (XSS).
2. Zero-day attack mitigation: Even when you think you're up-to-date, new vulnerabilities can pop up unexpectedly. A WAF is like having protection against "zero-day attacks," catching suspicious behavior before patches are available.
3. DDoS (Distributed Denial of Service) mitigation: Just as you handle challenges, a WAF helps your web application withstand DDoS attacks, distinguishing between friendly and malicious traffic.
4. Bot protection: Safeguard your web applications from malicious bots, blocking their harmful activities while allowing legitimate ones to thrive.
5. Enhanced logging and monitoring: Gain valuable insights with detailed logs and reports, empowering you to analyze incoming traffic and respond swiftly to potential threats.
6. Compliance requirements: For industries like finance and healthcare, a WAF is a mandated security measure to protect sensitive data, ensuring adherence to compliance standards.
7. Added layer of security: Strengthen your web application's defenses with an extra layer of protection from a WAF, complementing secure coding practices and regular security audits.
8. Real-time threat intelligence: Stay ahead of evolving threats with WAFs leveraging threat intelligence feeds, providing effective protection against the latest security risks.
A look into the OWASP Top 10 API Security Threats for 2023
Building upon these key takeaways, some of which are defined in the OWASP Top 10, you can further enhance your web application security and stay ahead of potential threats.
The Open Web Application Security Project (OWASP) Foundation, a non-profit organization, is committed to improving software security worldwide. One of its flagship initiatives is the OWASP Top 10, a list of the most common security vulnerabilities. This list, compiled from real-world data from web applications and other sources, serves as a detailed guide to help organizations understand and mitigate these threats. If you want to dive deeper into the meaning of each risk, find the official descriptions here.

Take the first step!
Having armed yourself with these crucial security insights, it's time to take your protection to new heights by exploring these 3 empowering possibilities that we offer you:
1. Application Endpoint Check:
A comprehensive security check for your web application that includes various types of endpoints such as REST, HTTP and GraphQL APIs. Our expert team will scan your application for potential vulnerabilities against the OWASP Top 10. You will receive detailed insights into your endpoint firewalls to proactively adress weaknesses and safeguard your web app from potential threats.
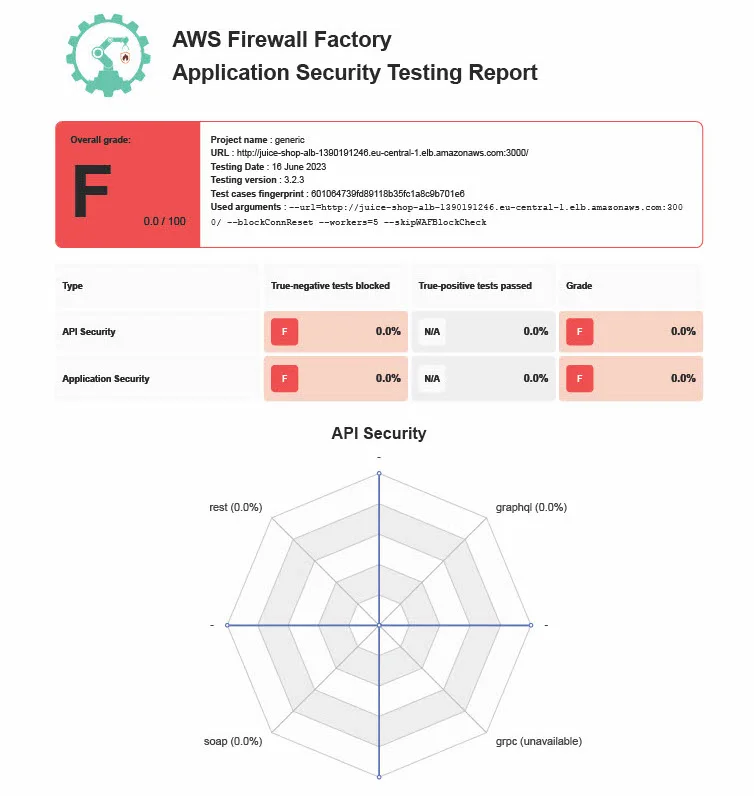
2. Web Application Firewall at Scale Workshop:
Join our 2-day workshop, whether you're a seasoned security pro or a newbie, and become proficient in designing, implementing, and managing firewalls at scale with ease.
Learn about AWS WAF Service, Firewall Manager, and key concepts, covering design principles, best practices for firewall management. Explore AWS Web Application Firewall basics, remediate vulnerabilities, and secure applications with managed rules while mitigating false positives, hands-on.
Elevate your security skills remotely, at your office, or our location for a flexible learning environment.
3. Web Application Firewall Implementation:
Designed to offer you a tailored WAF configuration that perfectly matches your evolving business needs while staying ahead of potential attacks, built by AWS Best Practices.
Our solution offers central governance and automation for your growing applications. With scalability in mind, your web application's security dynamically adapts to changing requirements and new threats.
Benefits of using the AWS Firewall Factory:
- Built by AWS Best Practices
- Full Automation for centralized WAF Deployment and Management at Scale
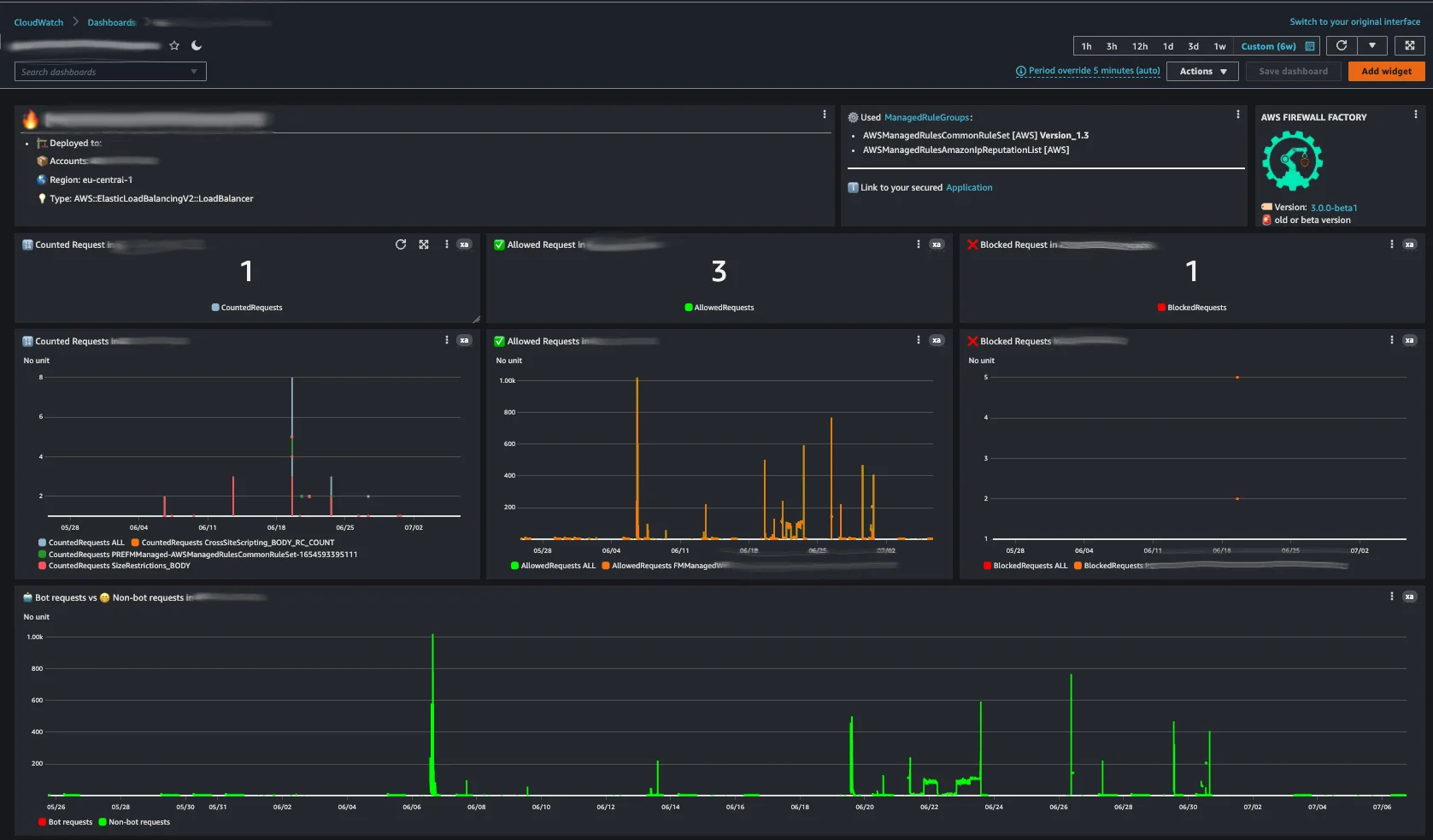
- Testing of the Web application with full comprehensive audit reports
- Additional features as centralized dashboards and centralized logging
- Automated cost calculation of Web Application Firewalls
Conclusion
With the rise of cloud environments as a prime target for attackers, investing in a Web Application Firewall (WAF) becomes crucial. It shields web applications against known vulnerabilities, zero-day attacks, DDoS threats, and malicious bots, while real-time threat intelligence fortifies the defense and ensures compliance with industry standards. Leveraging the power of the OWASP Top 10 further empowers organizations to understand and mitigate common vulnerabilities, proactively strengthening their defense against emerging risks.
If you are looking to take your API endpoints security seriously in 2023 - start off by picking a slot and chat with us about your security goals for free.
We use cookies on our website. Some of them are essential,while others help us to improve our online offer.
You can find more information in our Privacy policy
